|
|
| (16 intermediate revisions by 2 users not shown) |
| Line 1: |
Line 1: |
| − | ==ADVISE DoS Attack on AMI==
| + | Below are a list of example models built in Möbius. These examples come from the Mobius team and user community. '''Please consider sharing''' the models you have built in the past. If you do decide to share your model, please look at the [[Examples#Share_Your_Model|Share Your Model]] section for instructions on creating a new page and linking it here. |
| | | | |
| − | In this example, we will examine modeling a denial of service (DoS) attack on an advanced metering infrastructure (AMI) data collection unit (DCU) using ADVISE.
| + | == Examples == |
| | | | |
| − | ===Background===
| + | * [[SCADA Case Study from QEST 2011]] - A case study that uses the ADVISE formalism to study the security of a SCADA and corporate network. |
| | + | *[[ADVISE Bank Robbery Tutorial Model]]- An example using advise with full steps and project included. |
| | + | *[[Conveyor Belt]]- Incomplete |
| | + | *[[Database2]]- Incomplete |
| | + | *[[Ian2]]- Incomplete |
| | + | *[[Faulty Proc2]]- Incomplete |
| | + | *[[Multi-Proc]]- Incomplete |
| | | | |
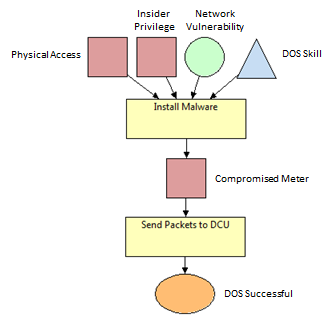
| − | In an AMI, multiple smart meters send data to a DCU. The DCU then aggregates meaningful information and forwards it to an appropriate location for analysis. In this scenario, we assume the adversary will DoS a DCU by flooding it with high volumes of meaningless traffic. Since each smart meter already contains an effective transmitter for communicating with the DCU, we assume that the most attractive attack is to install malware on the smart meters to convert the smart meters into renegade agents. Since the bandwidth of the traffic from a single renegade smart meter is limited, the addition of more renegade smart meters increases the effectiveness of the attack.
| + | == Share Your Model == |
| | + | Here is [[Example Model Template|the template]] that people should use. If you are not familiar with mediawiki here are steps involved in adding your own model. |
| | | | |
| − | In this example, we will examine the effectiveness of the DoS attack among adversaries of differing skill levels. For each adversary, we will also determine the most probable number of smart meters that have been converted to renegade agents to perform the attack.
| + | # Log in to https://www.mobius.illinois.edu/wiki/. |
| − | | + | # On the top right search for the name of the page you want to create. |
| − | ===Creating the Model===
| + | # If there are no matching results it should prompt you to create a page with the name that you searched for. |
| − | | + | # Under the page, create a submission by simply following the template of the [[Example Model Template|the template]]. Also, one has been created as an example for your reference and can be found [[Example Model Template|here]]. |
| − | To create the model for this attack, the analyzer must work backwards from the attack goals. In this example, there is only one attack goal: a successful DoS attack.
| + | # To view the source code of the page just click on the edit tab on the top right of the page. Copying the source code should have the format ready for you. |
| − | | + | # Under description you can simply copy your paper's Abstract section to give viewers a brief idea about your paper. Please be sure to link your paper and website. If you are confused about the syntax to create a link please refer to [https://www.mediawiki.org/wiki/Help:Links#External_links Links]. Also please upload your project by clicking on the [[Special:Upload]] link at the bottom of your page. |
| − | To reach the goal of successfully performing a DoS attack, the adversary must send traffic to the DCU. To send traffic to the DCU, the attacker must have access to at least one compromised meter. To gain access to at least one compromised meter, the attacker must install malware on at least one device. Installing malware on a device requires the adversary to have a certain level of DoS skill and either physical access to the targeted meter, insider privilege to the targeted meter, or a vulnerability in the AMI network.
| + | # If you have any questions feel free to contact Ken Keefe at [mailto:kjkeefe@illinois.edu kjkeefe@illinois.edu]. |
| − | | |
| − | [[File:ExampleAdviseDOS.PNG|center|alt=ADVISE model of a DoS attack on an AMI DCU.|An ADVISE model of a DoS attack on an AMI DCU.]] | |
| − | | |
| − | ===Implementing the Model===
| |
| − | | |
| − | First create three access blocks labeled “Physical Access,” “Insider Privilege,” and “Compromised Meter.” Next create a knowledge block labeled “Network Vulnerability” and a skill block labeled “DoS Skill”. Also create a goal block labeled “DoS Successful.”
| |
| − | | |
| − | Next, create an attack step labeled “Install Malware.” That attack step models the adversary installing malware on a single smart meter. The likelihood of the success of the "Install Malware" attack step is determined by the physical access available to the adversary, the insider privilege of the adversary, the knowledge of useful network vulnerabilities by the adversary, and the DoS skill of the adversary. If the "Install Malware" attack step is successful, the adversary gains access to a compromised meter.
| |
| − | | |
| − | To build the "Install Malware" attack step, make a connection from “Physical Access,” “Insider Privilege,” “Network Vulnerability,” and “DoS Skill” to the “Install Malware” attack step block. Next, make a connection from the “Install Malware” attack step block to the “Compromised Meter” access block. **Explain parameters | |
| − | | |
| − | Next, create an attack step labeled “Send Packets to DCU.” That attack step models the adversary sending traffic from the compromised meters to the DCU. The likelihood of the success of the "Send Packets to DCU" attack step is determined by the number of compromised meters in the system. If the "Send Packets to DCU" attack step is successful, then the adversary has successfully completed the DoS attack against the DCU.
| |
| − | | |
| − | To build the "Send Packets to DCU" attack step, make a connection from the “Compromised Meter” access block to the “Send Packets to DCU” attack step block. Then, make a connection from the “Send Packets to DCU” attack step block to the “DoS Successful” goal block.
| |
| − | | |
| − | TODO - Describe adversary details
| |
| − | | |
| − | ===Results===
| |
| − | | |
| − | ===Analysis===
| |
| − | | |
| − | ===Conclusion===
| |
| − | | |
| − | ==ADVISE Remote Disconnect Attack on AMI==
| |
| − | | |
| − | In this example, we will examine modeling a remote disconnect attack on an advanced metering infrastructure (AMI).
| |
| − | | |
| − | ===Background===
| |
| − | | |
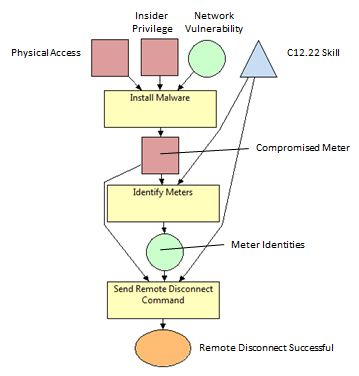
| − | In an AMI, the electric utility company has the capability to disconnect a client remotely. Remotely disconnecting a client is useful in situations such as the termination of the utility contract. Although the remote disconnect capability is intended to be used only by the electric company, the potentially disruptive capability is enticing to malicious adversaries. In this example, we will examine the effectiveness of the remote disconnect attack among adversaries of differing skill levels.
| |
| − | | |
| − | ===Creating the Model===
| |
| − | | |
| − | To create the model for the attack, the analyzer must work backwards from the attack goals. In this example, there is only one attack goal: a successful remote disconnect.
| |
| − | | |
| − | To reach the goal of successfully performing a remote disconnect, the adversary must send the remote disconnect command to the target smart meter. Before sending the remote disconnect command to the target smart meter, the adversary must first have access to a compromised meter in the AMI network, must know the unique identity of the target smart meter, and must have some skills using the C12.22 protocol. To learn the unique identity of the target smart meter, the adversary must identify the smart meter through the AMI traffic. To identify a smart meter identity, the adversary must have access to a compromised meter in the AMI network and have some skills using the C12.22 protocol. To compromise a smart meter on the AMI network, the adversary must install malware on the smart meter. Installing malware on a smart meter requires either physical access to the smart meter, insider privilege into the network, or knowledge of some relevant vulnerability in the AMI network.
| |
| − | | |
| − | [[File:ExampleAdviseRemoteDisconnect.PNG|center|alt=ADVISE model of a remote disconnect attack on an AMI meter.|An ADVISE model of a remote disconnect attack on an AMI meter.]] | |
| − | | |
| − | ===Implementing the Model===
| |
| − | | |
| − | *Accesses
| |
| − | **Physical Access
| |
| − | **Insider Privilege
| |
| − | **Compromised Meter
| |
| − | | |
| − | *Knowledges
| |
| − | **Network Vulnerability
| |
| − | **Meter Identities
| |
| − | | |
| − | *Skills
| |
| − | **C12.22 Skill
| |
| − | | |
| − | *Goals
| |
| − | **Remote Disconnect Successful
| |
| − | | |
| − | *Attack Steps
| |
| − | **Install Malware
| |
| − | **Identify Meters
| |
| − | **Send Remote Disconnect Command
| |
| − | | |
| − | *Adversary
| |
| − | | |
| − | ===Results===
| |
| − | | |
| − | ===Analysis===
| |
| − | | |
| − | ===Conclusion===
| |
| − | | |
| − | ==ADVISE Steal Customer Information Attack on AMI==
| |
| − | | |
| − | In this example, we will examine modeling the stealing of customer information from an advanced metering infrastructure (AMI).
| |
| − | | |
| − | ===Background===
| |
| − | | |
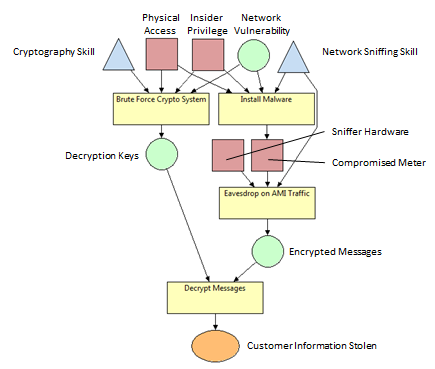
| − | In an AMI, client smart meters send customer information to the electric utility company over an encrypted channel. Since the customer information sent from the client smart meters contains some personal information about the customer, an adversary may want to intercept the traffic to access the available personal information about the customer. In this example, we will examine the effectiveness of stealing customer information among adversaries of differing skill levels.
| |
| − | | |
| − | ===Creating the Model===
| |
| − | | |
| − | To create the model for the attack, the analyzer must work backwards from the attack goals. In this example, there is only one attack goal: successfully stealing customer information.
| |
| − | | |
| − | To reach the goal of successfully stealing customer information, the adversary must decrypt encrypted messages using the appropriate decryption keys. To obtain the appropriate decryption keys, the adversary must brute force the cryptography system of the AMI network. To brute force the cryptography system of the AMI network, the adversary must have adequate cryptography skills and access to the AMI network. The three ways to have adequate access to AMI network are to have physical access to the system, insider privileges to the AMI network, or knowledge of a useful vulnerability in the AMI network.
| |
| − | | |
| − | To access the encrypted messages, the adversary must eavesdrop on the AMI traffic. To eavesdrop on the AMI traffic, the adversary must have adequate network sniffing skills and a way to sniff the network traffic. The two ways to sniff network traffic are to either have appropriate sniffer hardware or have access to a compromised meter. To compromise a meter, the adversary must install malware on a meter. To install malware on a meter, the adversary must have adequate network sniffing skills and access to the meter. The three ways to have adequate access to AMI network are to have physical access to the system, insider privileges to the AMI network, or knowledge of a useful vulnerability in the AMI network.
| |
| − | | |
| − | [[File:ExampleAdviseStealCustomerInfo.PNG|center|alt=ADVISE model of a stealing customer information attack on an AMI meter.|An ADVISE model of a stealing customer information attack on an AMI meter.]] | |
| − | | |
| − | ===Implementing the Model===
| |
| − | | |
| − | *Access
| |
| − | **Physical Access
| |
| − | **Insider Privilege
| |
| − | **Sniffer Hardware
| |
| − | **Compromised Meter
| |
| − | | |
| − | *Knowledge
| |
| − | **Network Vulnerability
| |
| − | **Decryption Keys
| |
| − | **Encrypted Messages
| |
| − | | |
| − | *Skills
| |
| − | **Cryptography Skill
| |
| − | **Network Sniffing Skill
| |
| − | | |
| − | *Attack Steps
| |
| − | **Brute Force Crypto System
| |
| − | **Install Malware
| |
| − | **Eavesdrop on AMI Traffic
| |
| − | **Decrypt Messages
| |
| − | | |
| − | *Adversary
| |
| − | | |
| − | ===Results===
| |
| − | | |
| − | ===Analysis===
| |
| − | | |
| − | ===Conclusion===
| |
| − | | |
| − | == <span style="font-size:120%">Möbius</span> ==
| |
| − | | |
| − | === <span style="font-size:110%">Motivation</span> ===
| |
| − | | |
| − | ==== <span style="font-size:106%">''Solution''</span> ====
| |
| − | | |
| − | <span style="font-size:102%">'''Graph'''</span>
| |
| − | | |
| − | <span style="font-size:108%"><span style="font-variant:small-caps">Edit</span></span>
| |
| − | <span style="font-size:115%">Möbius</span>
| |
| − | <span style="font-size:125%"><font face=Courier>Documentation</font></span>
| |
| − | | |
| − | “” –
| |
| − | | |
| − | <equation id="eqn:binom" shownumber>
| |
| − | <center><math>f(k)=\binom{n}{k}p^k(1-p)^{n-k}\quad k=0,1,\dots,n</math></center>
| |
| − | </equation>
| |
| − | | |
| − | Sort of like <xr id="eqn:binom" />, but not really.
| |
| − | | |
| − | | |
| − | == References ==
| |
| − | <references />
| |
Below are a list of example models built in Möbius. These examples come from the Mobius team and user community. Please consider sharing the models you have built in the past. If you do decide to share your model, please look at the Share Your Model section for instructions on creating a new page and linking it here.